Java Security Sandbox improperly allows
access to any photo on your computer
(September 4, 2013; VU#822710; S0391650; other vulnerabilities)
|
UPDATE: It appears that Java 7 update 51 fixes this security hole.
|
The Security Hole: Applet.getImage() in Java 7 and Java 6 allows a SANDBOXED
applet to access any photo on your computer via the file:// protocol.
I leave it as an exercise for Oracle to determine if Applet.getAudioClip()
is also vulnerable.
Tested versions: Java 1.7.0_40, 1.7.0_25, 1.7.0_21, 1.6.0_45 and 1.6.0_01 all have the flaw.
jview 1.1.4, Java 1.4.1_05 and 1.5.0_01 do not have the flaw,
so the flaw appears to have been introduced into Java in version 1.6 (May 2007).
Isn't it amazing that Sun/Oracle has no automated testing procedures in
place to catch this blatant security violation of the security sandbox?
It is no wonder that Java is plagued by security holes, because Oracle is
shipping Java without even the most basic automated security tests in place.
Mitigating Factor: The applet must know the filename of a photo on the local
computer.
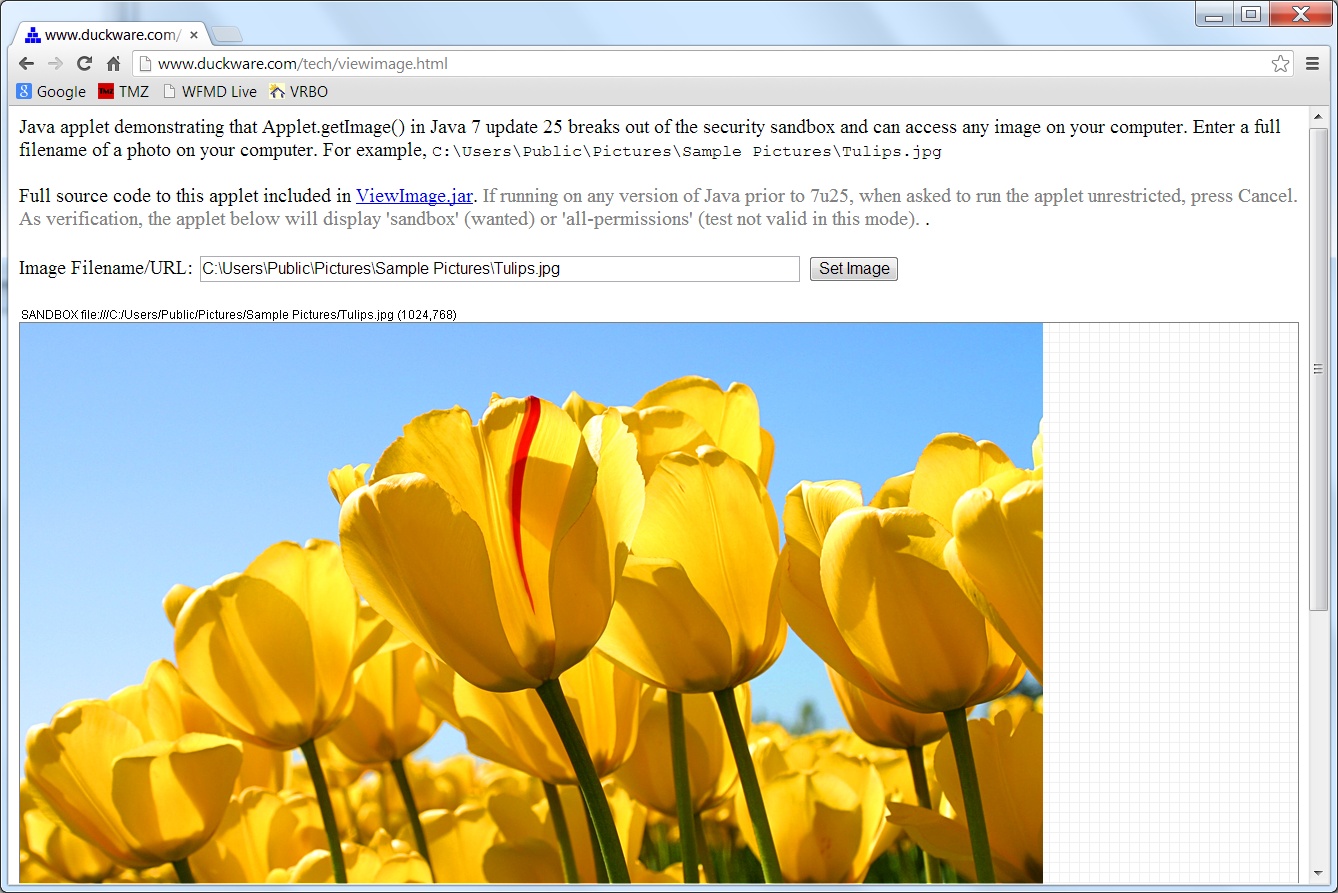
Live Interactive Demonstration: Visit viewimage.html and run the
sandboxed applet there. Enter the full filename to a photo on your local computer. For example,
C:\Users\Public\Pictures\Sample Pictures\Tulips.jpg or
C:\Windows\Web\Wallpaper\Landscapes\img11.jpg, etc.
This is what I see on my computer — a sandboxed applet running from duckware.com,
accessing an image on my local computer, breaking out of the sandbox:
|
|